In the late 20th century, scientists made biogenetic history when they successfully cloned a mammal, Dolly the sheep, for the first time. Now, in the 21st century, industrial history is being made again with the development of a new phenomenon in the same realm of duplication, except this time it’s digital. We call it Digital Twin.
With the advent of Industry 4.0, an increasing number of organizations have implemented digital twin technology to optimize their performance, enhance their educational initiatives, or facilitate advanced maintenance. Even the automotive industry has readily embraced this transformational technology. However, organizations must acknowledge that the adoption of digital twin technology may simultaneously expose them to potential cyber threats. Thus, securing digital twins within an organization should be viewed as an essential priority, on par with their implementation.
In this blog, we shall first explicate the fundamental concept of digital twin technology. Next, we shall examine how the implementation of digital twins has imparted significant benefits to the automotive industry in particular. Finally, we shall address the cybersecurity issues that organizations must tackle. This will encompass safeguarding digital twins from theft and protecting them from being compromised, whether virtually or physically.
Digital Twins: Past and Present
A digital twin is a digital representation of an intended or actual real-world physical product, system, or process that serves as an effectively indistinguishable digital counterpart for practical purposes, such as simulation, integration, testing, monitoring, and maintenance. [2][3]
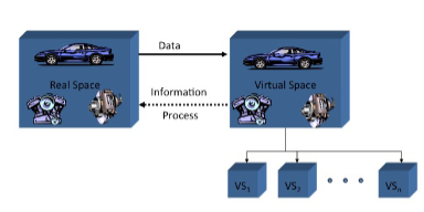
The concept and model of the digital twin were first publicly introduced in 2002 by Michael Grieves and was named the Product Lifecycle Management (PLM) model. The PLM model aims to create real and virtual spaces to store information for both domains. The following picture provides a glimpse of the PLM model. [3]
Figure 1: The Concept and Model of the Digital Twin
In 2010, NASA’s John Vickers coined the term “digital twin”. Michael Grieves and John Vickers [3] re-emphasized the concept of the digital twin derived from the PLM model. In fact, at this point, NASA has been using virtual replicas of spacecraft and aircraft for years to study or simulate the real systems.
The fundamental concept of digital twins [5] can be summarized as follows:
- Digital twins are fed with real-time data from their physical systems.
- Control and action commands are transmitted from the digital twin back to the physical system.
- The synchronization between the digital twin and physical entity ensures that the production systems are continuously optimized, as the digital surrogates receive real-time performance information from the physical system.
Figure 2: The Fundamental Concept of Digital Twins
The Implementation of Digital Twins in the Automotive Industry
The implementation of digital twin technology has been widely adopted by various industries, ranging from small-scale machine components to large-scale urban environments. In this section, we shall examine how the automotive industry has embraced this transformative technology and the consequential benefits reaped by car manufacturers.
1. Exploring the Benefits of Digital Twins in the Automotive Industry
Firstly, digital twins help manufacturers to improve their productivity. Manufacturers can duplicate a physical entity into a virtual one. Using a virtual entity, manufacturers can evaluate performance based on different scenarios and identify flaws or potential problems during simulations. By conducting various tests on the virtual entity, they can reduce product failures and improve the development process.
Secondly, digital twins can monitor and manage products and systems in real-time, thus increasing production efficiency. Moreover, feedback data from sensors and IoT devices can help manufacturers determine the health of the production site and conduct predictive maintenance.
Thirdly, digital twins can be used for educational purposes. Manufacturers can train their employees using a virtualized entity, without having to set up a real environment. Furthermore, employees can be trained remotely.
Lastly, digital twins can enhance sales. By using digital twins, customers can visualize how a product works. Manufacturers can utilize digital twins to help customers understand new features, customize products on demand, or compare old designs to fulfill their needs [4].
2. Examining Automotive Manufacturers’ Implementation of Digital Twins
When discussing pioneers of modern technology, Tesla is a prominent example. Tesla [6] has adopted digital twin technology by creating a virtual replica for each car they have sold. Sensor data from thousands of cars, apps, and even superchargers continuously stream into each car’s simulation at the factory. This allows them to monitor whether the car is operating as expected or requires further maintenance.
Renault and Ford, traditional car manufacturers, have also readily adopted digital twin technology. Renault [7] has described how they implemented digital twin technology in mid-2022. They create a virtual model at the design stage and conduct various tests before creating a physical twin. After the physical twin is manufactured and sold, feedback data based on real-world usage is fed back to the digital twin. This enables them to optimize their workflow and reduce the time taken to design a new vehicle from an entire year to just one quarter.
Ford has also leveraged digital twin technology to enhance product design. For instance, Ford [8] developed a headlight system that notifies the driver when approaching corners. They created a digital twin to simulate how light falls and reflects in the physical world. With this simulation, they developed a new driving light system that enhances driving safety at night.
Nissan [9] has leveraged digital twin technology with a specialized term, “predictive digital twin.” Digital twins at Nissan are used to model production scenarios and identify crucial bottlenecks in the sealing process, among other things. With accurate simulation, they have not only saved money on certain processes but also maintained high productivity levels.
Navigating Cybersecurity Challenges and Issues in the Automotive Industry
The benefits of digital twin technology in augmenting productivity and efficiency notwithstanding, the adoption of this popular technology poses several security challenges and issues. Consequently, it is imperative to consider the following key security issues before implementing digital twin technology. [10][11]
1. Reconnaissance
Reconnaissance involves packet sniffing and bandwidth sniffing. Attackers may use these techniques to enumerate devices, discover vulnerabilities, and identify security loopholes. Such attacks can result in the unauthorized retrieval of confidential data and the exploitation of vulnerabilities in both the CPS and its digital twin.
For instance, attackers can intercept network packets and monitor network activities to determine which components of the CPS are active or to infer the CPS activity based on the bandwidth used between the CPS and its digital twin. Even if the network packets cannot be fully decrypted or parsed, attackers may still be able to estimate the possible protocols based on the bandwidth between the CPS and its digital twin.
Once attackers have successfully intercepted network traffic, they can gain insight into how the CPS communicates with its digital twin. In the following section, we will discuss attacks that are based on reconnaissance, including data injection, data delay, and model injection.
 Figure 3: Bandwidth Sniffing Attacks on CPS and Digital Twin
Figure 3: Bandwidth Sniffing Attacks on CPS and Digital Twin
2. Data Injection Attacks
Due to the inherent data dependency and need for consistency between the physical and virtual entities, communication between them must be carefully managed. One attack technique involves injecting malicious commands or false status reports to deceive the system. Below are some attack techniques that can either disrupt the cyber-physical system or provide false information to digital twins.
1) Attackers send specific commands, which should originate from the digital twin, to take control of the CPS. Such attacks may seek to either control CPS devices or damage and destroy them, rendering the digital twin incapable of controlling the CPS and potentially causing simulation failures.
Figure 4: Attacker can seize control of CPS by injecting fault commands
2) Attackers send packets that are intended to represent the status of the CPS to deceive digital twins. This type of attack can cause the digital twin to receive incorrect data from the CPS, leading to confusion and incorrect operation.
3. Data Delay Attack
Synchronization in real-time between the virtual and physical entities is a crucial aspect of digital twin technology. However, attackers may attempt to disrupt this synchronization by introducing significant delays during communication. Attackers may flood the network to impact either the digital or physical twin and cause such delays.
This type of attack is similar to a denial-of-service (DoS) attack. Attackers don’t even need to understand ICS protocols or functionalities to execute such an attack. When a timeout occurs, either the digital or physical twin may fail to respond in time, resulting in unexpected behavior from both twins.
Figure 5: Attacker Can Cause Total Network Paralysis with Dos Attack
4. Model Corruption
Another method to disrupt synchronization between the digital and physical twins is to directly inject malicious code. For instance, if an attacker gains access to the environment, they may search through the repositories, inspect the code, and inject malicious code to corrupt the model. Once the model is compromised, the digital twin is also affected. The digital twin may no longer be able to accurately represent the physical twin, resulting in inconsistencies in the output.
Figure 6: Injecting Malicious Code to Disrupt Synchronization in Digital Twin
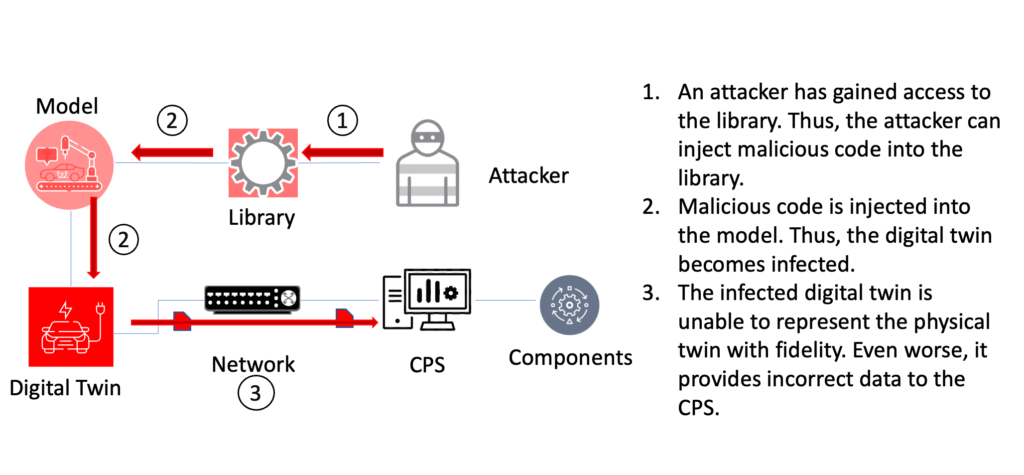
Alternatively, attackers can inject malicious code into the libraries that are used to construct the model. Models built with infected libraries are also corrupted. Consequently, it is possible that the digital twin may become compromised and no longer be able to accurately represent the physical twin, leading to inconsistencies in the output.
Figure 7: Injection of Malicious Code into Libraries
One of the challenges of implementing digital twin technology is maintaining consistency between the physical and virtual twins. In the case of a model corruption attack, it can be difficult to detect the issue, as developers may not notice the problem until they inspect the repository or run jobs on an infected digital twin. Running an infected digital twin not only leads to inconsistencies, but it can also compromise the CPS, as the malicious code sent by the infected twin may cause additional harm.
5. IP Leakage and User Data Breach
Once digital twin technology is breached, attackers can potentially gain access to sensitive data that is collected by the physical twin, including sensor values, data from IoT devices, and more. Typically, this data cannot be easily accessed in a factory environment. However, with a leaked digital twin, sensitive data can be more easily retrieved. Moreover, the physical twin may include valuable intellectual property (IP), which is often a critical asset for companies.
Furthermore, many organizations today place a high priority on protecting privacy, as exemplified by GDPR. If a digital twin is breached and includes customer information, the organization may suffer not only financial losses but also damage to its reputation[11].
How To Protect Digital Twins
In today’s world, the importance of securing digital twin technology cannot be overstated. To safeguard your organization, here are some recommended best practices for protecting your digital twins.
1. Control Network Access:
Implementing proper access control lists (ACLs) is an essential step in preventing illegal access from external sources. This practice helps to safeguard all aspects of an organization, including the cyber-physical system (CPS) and digital twin, from unauthorized access.
2. Verify Data Integrity:
Verifying each data transmission to either the digital twin or CPS is crucial. Major industrial control system (ICS) protocols have their own methods for securing communication, which can prevent attackers from sniffing data or injecting incorrect commands and/or statuses. For instance, Modbus/TCP [13] has established security principles to safeguard data transmission:
1) 509v3 certificate-based identity and authentication with TLS
2) Mutual client/server TLS authentication
3) Authorization using roles transferred via certifications
3. Prevent Flooding Attacks
This is particularly important for digital twins due to the real-time nature of their operations. Here are some ways to defend your network against such attacks:
1) You can monitor normal activities to establish a network baseline, including:
a. Number of packets
b. Size of data transmitted/received
c. Data load of digital twin/CPS
2) You can implement (D)DoS protection mechanisms to prevent these types of attacks.
4. Prevent any Unexpected Modifications
It has been discovered that attackers can inject malicious code to break consistency. To protect your code repositories (i.e., model and library), consider implementing the following mitigations.
1) Access control should be applied carefully, as we have discussed in 1.
2) Allow only digitally authorized models to integrate with the digital twin.
3) Check out the library integrity before integration. This could be done by calculating and validating checksum.
References
[1] Digital twin, Digital twin, Wikipedia, Accessed Feb 2023.
[2] Dr. Michael Grieves and John Vickers, Origins of the Digital Concept, Digital Twin Institute, August 2016.
[3] IBM, What is a digital twin?, IBM, Accessed Feb 2022.
[4] Hazal Şimşek, Top 5 Use Cases of Digital Twin in Automotive Industry in ’23, AI Multiple, January 1, 2023.
[5] Guodong Shao, Deogratias Kibira, DIGITAL MANUFACTURING: REQUIREMENTS AND CHALLENGES FOR IMPLEMENTING DIGITAL SURROGATES, 2018 Winter Simulation Conference, December 2018.
[6] Jesse Coors-Blankenship, Taking Digital Twins for a Test Drive with Tesla, Apple, IndustryWeek, April 29, 2020.
[7] Renault Group, Vehicle Digital Twin: When Physical and Digital Models Unite, Renault Group, June 21, 2022.
[8] Ford, Ford’s New Headlights are Ahead of the Curve When it Comes to Making Night Driving Easier, Ford Media Center, April 22 2021.
[9] Lanner 5 Digital Twins that are Helping Nissan Boost Productivity, Lanner, August 21, 2018.
[10] Tomas Kulik, Cl´ audio Gomes, Hugo Daniel Macedo, Stefan Hallerstede, and Peter Gorm Larsen, Towards Secure Digital Twins, LNCS, volume 13704, October 17, 2022.
[11] David Holmes, Maria Papathanasaki, Leandros Maglaras, Mohomed Amine Ferrag, Surya Nepal, Helge Janicke, Digital Twins and Cyber Security – solution or challenge?, SEEDA 2021, August 2021.
[12] Modbus.org, MODBUS/TCP Security, Accessed Feb 2022.